Cloud platforms pose data security challenges with remote servers and third-party providers like Amazon. Our tailored solutions simplify robust security measures, protecting sensitive data in an insecure cloud landscape.
Request a demo+ Data can be computed on/with
- Data is unprotected
+ Data is protected
- Data can not be computed on/with
+ Data is protected
+ Data can be computed on

3rd place winner
Our unique set of 4 key properties
Secure end-to-end with formally verified guarantees. Anyone can claim to be secure, talk is cheap.
Combining software mechanisms and hardware mechanisms from extensible sets. Inherently independent of mechanisms/platforms!
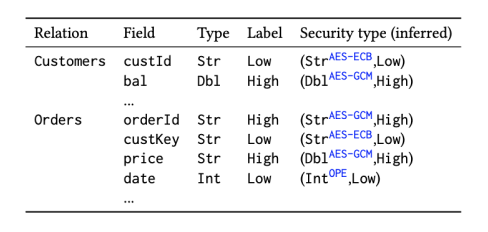
Data analysts write queries agnostically to security constraints. No need for security annotations!
Over 10x faster than state of the art9. Low overhead is key to practicality and adherence to security!
We target the confidential analytics market
Confidential computing market will :
Confidential analytics market expected to be 10% of confidential computing

Built on Spark, leading platform for distributed data analytics
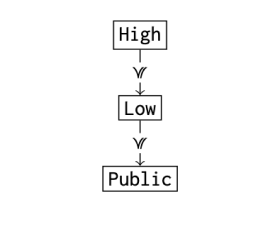
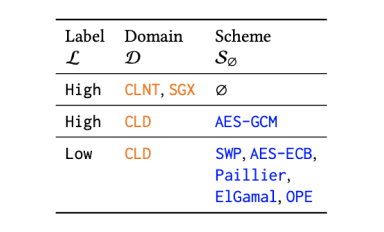
Leverages intuitive novel security policy with custom security levels (e.g., secret/top secret) assigned to soft- and hardware mechanisms
Formal framework for verifying security based on noninterference
Example security policy setup
More efficient than generic computing platforms (Fortanix, Decision3, Veracruz, Teaclave).
Based on over 10+ years of research experience in confidentiality — preserving data processing — over $3.4 Mio public and corporate funding raised.
Inherently more flexible and efficient than closest related offerings
Trustworthy approach with no backdoors (required by US and Chinese governments for their corps), supporting digital sovereignty.
For small financial businesses.
For mid-size financial institutions.
For large financial institutions and banks.
Over 50 years of experience in research and business





Begin safeguarding your business by taking the first steps toward enhanced security measures. Implement foundational shields against potential risks.
Request a Demo